With the rise of ransomware against hospitals, attacks against the Democratic National Committee (DNC), and even major tech CEOs getting hacked, no one is immune to having their information stolen. Today’s attackers are sophisticated, state sponsored, and armed with advanced techniques to hit specific targets. Despite an estimated $75 billion per year spent on security, adversaries dwell undetected in networks for an average of 146 days—exposing organizations to massive theft and business disruption. Organizations must work to close this gap and thwart advanced threats before damage and loss occur.
Endgame helps organizations close the protection gap with a unified platform for preventing, detecting, hunting, and responding to known and unknown threats at the earliest stages of a cyberattack. Endgame enables Security Operations Center (SOC) and Incident Response (IR) teams to automate the threat hunting process, from asset discovery to response, dramatically reducing the time to detection and remediation. Time ordinarily spent on forensic analysis and compromise assessment can be shifted to attack detection and response, pre-empting advanced attacks, and discovering and eliminating intruders before they cause damage and loss.
The Endgame platform does not depend on signatures or indicators of compromise (IOCs). Rather it draws on machine learning and other advanced analytics to detect not only malware, but patterns and signals of maliciousness. The Endgame platform is built to discover attackers even when they are dormant, as in the case of the DNC attacks, or missed by traditional signature-based tools, reducing the time and cost associated with incident response and compromise assessment.
The hunt for APTs
The DNC attack was attributed to two different groups: APT28, or Fancy Bear, and APT29, or Cozy Bear. APT28 is a Russian-based threat actor that has been active since the mid-2000s. APT29 is the adversary group that last year successfully infiltrated the unclassified networks of the White House, State Department, and U.S. Joint Chiefs of Staff. Both APT28 and APT29 have been responsible for targeted intrusion campaigns against the aerospace, defense, energy, government, and media sectors, among many others.
Imagine a large enterprise with a SOC team consisting of tier 1, tier 2, and tier 3 security analysts. The tier 1 and tier 2 analysts are focused on monitoring the flood of alerts and determining their root causes; high-priority alerts are then escalated to tier 3 analysts for resolution. Now imagine this large enterprise is at the receiving end of targeted attacks by groups using similar techniques as APT28 Fancy Bear and APT29 Cozy Bear.
Unfortunately, this large enterprise is likely susceptible to being breached because techniques used by APT28 and APT29 can bypass their existing security products, and there are no known indicators of compromise (IOCs) or signatures of these attacks that this large enterprise can rely on.
Using the recent DNC attack from APT29 Cozy Bear as an example, we’ll demonstrate how Endgame’s platform empowers security analysts to find never-before-seen, persistent attackers and evict them. With Endgame’s platform deployed, we’ll detect these attackers hiding in the network and remove them before critical assets are stolen.
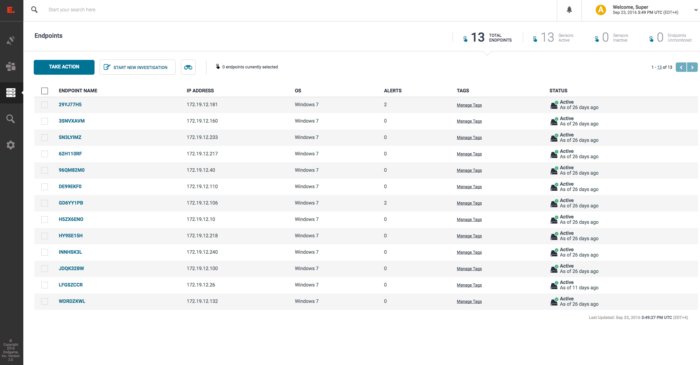
Figure 1: From the Endgame dashboard, security analysts can survey, investigate, and remediate endpoints. The top-right corner shows new alerts and the number of endpoints on which Endgame is deployed.
Surveying the network
Endgame operates with the basic premise that enterprises have already been compromised, and therefore, SOC teams should proactively look for threats within their network before damage and loss of information occurs. With Endgame, analysts can simply enter network IP address information to scan the network and gain situational awareness of endpoints and device connections. Once the security analyst identifies all critical assets that need monitoring, they can deploy the lightweight Endgame sensor to Windows and Linux endpoints with a single click. Endgame also supports out-of-band deployment through endpoint management tools such as Microsoft’s System Center Configuration Manager and IBM’s BigFix.
There are two modes of operation for Endgame sensors: dissolvable or persistent. The analyst can choose to use a dissolvable sensor to conduct a short-term hunt mission or leverage the persistent mode to continuously monitor and explore the enterprise network.
Endgame operates in stealth mode to hide its presence from the adversary. This means that the adversary will not find an Endgame process running on the system and will not be able to disable it or tamper with it. Once the sensor is deployed, the analyst will begin to receive alerts, which are generated by Endgame’s heuristics and behavior detections when attackers’ techniques are encountered.
Hunting for malicious persistence
In the example of the recent DNC hack, APT29 persisted for almost a year in the network. Sophisticated persistence techniques are commonly used by attackers to ensure ongoing presence on compromised systems even when those systems are shut down and restarted. Persistence is a characteristic of every major compromise, and attackers are constantly rotating and evolving persistence techniques to evade detection and stay hidden in an environment after every reboot.
The APT29 attack relied primarily on the SeaDaddy implant written in Python and a PowerShell backdoor, with persistence accomplished via Windows Management Instrumentation (WMI) service that allowed the attacker to launch malicious code automatically after a specific period of system uptime or on a specific schedule.
Endgame’s platform covers more than 27 persistence techniques without relying on IOCs or signatures. Many of these techniques are enumerated in the MITRE Attack Matrix, a framework used widely by practitioners to categorize the techniques used by attackers when operating in an enterprise network. Endgame shares its discoveries of new attack techniques with MITRE to ensure that enterprise defenders are fully informed about new adversary behavior, including the recent addition of a new persistence technique to the model.
With Endgame deployed on enterprise endpoints, the security teams receive alerts on suspicious activity. Alerts provide filename, full path, an Endgame MalwareScore, and an MD5 hash to identify malicious activity. Further, SOC teams can run automated investigations to hunt for persistence techniques, such as those used by APT29.
Endgame’s advanced analytics detect suspicious persistence locations to quickly narrow the scope of the problem. By providing this powerful, comprehensive automated capability, analysts no longer have to manually export data and analyze them with spreadsheets to determine suspicious behavior, thus saving significant time to detection.
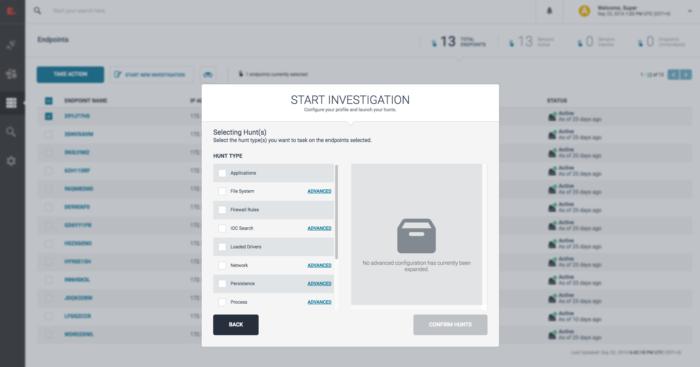
Figure 2: With a few clicks, SOC analysts can launch investigations across a variety of resources to hunt for malicious behavior and infected boxes.
The analysis—shown below—results in a histogram view of unique occurrences among a population of endpoints. With this view, we can see that Endgame was able to detect a novel persistence technique used by APT29 without prior knowledge and with only a few clicks.
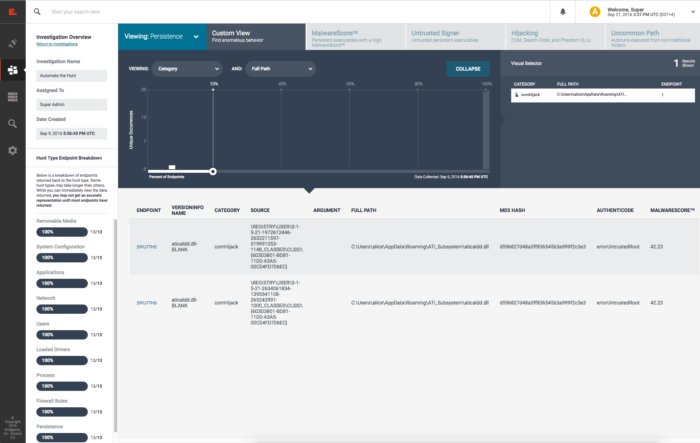
Figure 3: Security analysts use Endgame’s investigation view to identify malicious persistence and take action.
Hunting for malicious files
In addition to hunting for the APT29 persistence technique on compromised systems, the launch of the malicious code will trigger a prioritized alert. By clicking on the alert, the security analyst can view the Endgame MalwareScore, which provides a score of confidence for the malicious files. Our signature-less malware classification capability uses a gradient-boosted decision tree data science model on the lightweight sensor with low false-positive rates. To investigate further, the security analyst can launch a hunt for running processes, find the malware and the endpoint infected, and kill the process with zero business disruption. With a few clicks, a tier 1 analyst can not only investigate the alert, but also remediate any issues with zero business disruption.
Endgame gives SOC, threat hunting, and IR teams a combination of prevention, detection, and response capabilities to protect their infrastructures. Beyond the examples outlined above, Endgame allows analysts to further their investigations by executing additional hunts for persistence, privilege escalation, defense evasion, or credential theft. Furthermore, the analyst can leverage automated collection of information on network connections, files, processes, registries, system configurations, and users to provide contextual information for more extensive investigation. Endgame presents all of the data for an investigation in a single real-time view for analyst review.
By automating the hunt, Endgame allows organizations to protect themselves against both known and never-before-seen attacks. Most important, it allows analysts to identify and thwart these attacks before damage and loss occur.
Jian Zhen is senior vice president of products at Endgame.
New Tech Forum provides a venue to explore and discuss emerging enterprise technology in unprecedented depth and breadth. The selection is subjective, based on our pick of the technologies we believe to be important and of greatest interest to InfoWorld readers. InfoWorld does not accept marketing collateral for publication and reserves the right to edit all contributed content. Send all inquiries to newtechforum@infoworld.com.
















