Licensed for Distribution
This research note is restricted to the personal use of ().Magic Quadrant for Managed Security Services, Worldwide
Published 2 May 2019 - ID G00354867 - 73 min read
By Analysts Toby Bussa, Kelly Kavanagh, Sid Deshpande, Pete Shoard
Managed
security services is a market that is diversifying to meet the demands
of a wide range of buyers. Security and risk management leaders should
identify providers best aligned to their requirements, security
maturity, and organization’s vertical, size, and geographic footprint.
This Magic Quadrant is related to other research:
Critical Capabilities for Managed Security Services, Worldwide
Market Definition/Description
Gartner defines managed security services (MSSs) as:
- The remote 24/7 monitoring of security events and security-related data sources
- The administration and management of IT security technologies
- The delivery of security operation capabilities via shared services from remote security operations centers (SOCs), not through on-site personnel nor remote services delivered on a one-to-one basis to a single customer
The core service
of most MSS providers (MSSPs) are 24/7 security event monitoring and
response for threat detection use cases, and reporting for compliance
use cases across a technology-agnostic range of log event and data
sources.
In addition to security
event monitoring and response services, MSSPs’ portfolios usually
include one or more of the following managed services, in addition to
other services that may be specific to the MSSP’s core market (e.g., IT
outsourcing or telecommunications):
- Security technology administration and management of firewalls, unified threat management (UTM), intrusion detection and prevention system (IDPS), endpoint protection platform (EPP), endpoint detection and response (EDR), secure web gateway (SWG) and secure email gateway (SEG)
- Incident response services (both remote and on-site)
- Vulnerability assessment and managed vulnerability management services (e.g., scanning, analysis and recommendations/remediation)
- Threat intelligence services (e.g., machine-readable threat intelligence feeds, customer-specific dark web and social media monitoring)
- Managed detection and response (MDR) services
MSSPs
increasingly offer a wider and more varied set of services; however,
Gartner clients are primarily interested in contracting MSSPs for 24/7
remote security event monitoring and response services. They are seeking
to address threat detection use cases and to add additional
capabilities to fill gaps in their security controls and capabilities as
needed (e.g., incident response or vulnerability management). Remote
technology administration and management, while offered by many MSSPs,
is highly commoditized now and increasingly less important to Gartner
clients interested in MSSs. Meeting compliance requirements is also
rarely mentioned outside of some specific verticals and regions. As
Gartner clients pursue cloud-oriented and cloud-first approaches, the
scope of security monitoring service requirements is also expanding. It
includes monitoring of cloud-delivered services, both SaaS and IaaS, as
well as operational technology (e.g., ICS/SCADA) environments and
Internet of Things (IoT) devices. This reflects the expansion of
security event monitoring beyond the confines of an MSS buyer’s
on-premises perimeter.
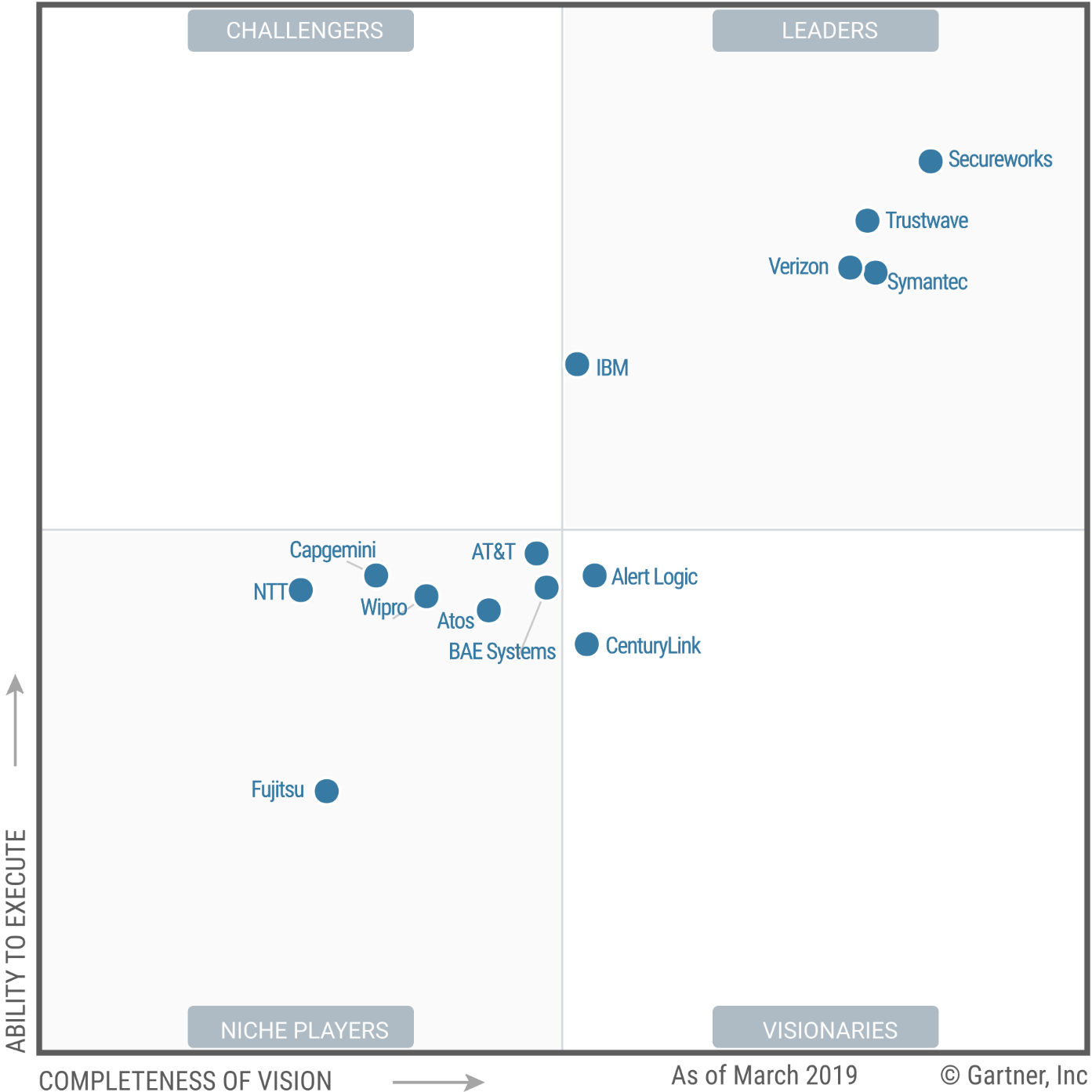
Magic Quadrant
Vendor Strengths and Cautions
Alert Logic
Alert
Logic, based in Houston, Texas with primary offices in Austin, Texas,
London and Cardiff, U.K., Cali, Colombia, and Tokyo, provides a range of
services delivered from 24/7 SOCs in Houston and Cardiff. Alert Logic’s
footprint and marketing is primarily focused on North America and
Europe, but it has a primary partner in Japan, and a variety if channel
partners for Asia/Pacific and Latin America.
Alert
Logic’s services are focused around 24/7 security event monitoring,
threat detection and response, and vulnerability management of public
and private cloud services (i.e., IaaS), as well as on-premises and
hybrid environments. They market this approach as “SIEMless Threat
Management.” Three tiers of services are available — Essentials,
Professional and Enterprise — that are aimed at a range of buyers, from
midsize enterprises to large, global enterprises. Additional services
include ActiveWatch Enterprise and a managed web application firewall
(WAF). Alert Logic has a threat research and intelligence team for
feeding proprietary threat intelligence to its monitoring platform.
Threat hunting as a service is an option, and professional services are
available as needed to assist with security assessments, service
implementation and onboarding.
MDR-type
services are provided by Alert Logic using its proprietary technologies
for threat prevention, detection and response, e.g., network intrusion
detection, log monitoring and web application firewall. Alert Logic’s
delivery platform uses Amazon Web Services (AWS), leveraging specific
AWS Regions to support data residency requirements.
Alert
Logic is a good shortlist candidate for buyers who are underinvested
and under-resourced in key security operations capabilities like 24/7
security event monitoring and response, and vulnerability management. It
is also a good candidate for companies that are mature but need to
augment their existing capabilities with specific threat detection and
response services. Buyers who need to support multiple cloud or hybrid
environments sourced with a single provider should also consider Alert
Logic.
Strengths
- Alert Logic’s services focus on the core security services, e.g., asset and vulnerability management, 24/7 security monitoring and response delivered through an easy-to-use and easy-to-navigate portal.
- Buyers heavily invested in, or planning to migrate to, AWS and Microsoft Azure, especially those who leverage containers within IaaS, will benefit from Alert Logic’s asset and vulnerability assessment technology. It can scan traditional assets, but also support container scanning, which is a differentiator in the MSS market. In addition, AWS buyers will benefit from Alert Logic’s ability to identify configuration-based exposures.
- Alert Logic has extensive support for providing security services for AWS and Azure customers, including asset management, vulnerability management including container vulnerability assessment, and 24/7 threat monitoring, detection and response. Alert Logic was a launch partner for AWS’ Security Hub service.
- The tiered pricing model is easy to understand and offers an upgrade path for buyers who want to start with basic security hygiene services and grow into the security monitoring and response services. Pricing is primarily based on nodes monitored across the customer’s environment, with separate monthly recurring pricing for ActiveWatch Enterprise and managed web application firewall. Customers can purchase Alert Logic services directly from a network of reseller partners and via the AWS Marketplace.
- Alert Logic receives higher-than-average customer reference scores for overall experience, integration and onboarding, ongoing service and support, and product capabilities. Customers willing to recommend Alert Logic to others and to renew their services are also rated positive.
Cautions
- Alert Logic’s incident response capability currently supports a limited set of response actions, like threat investigation and blocking response actions via Alert Logic’s proprietary technology stack at the network and web app layers. Support for endpoint protection (and associated response actions) was announced as beta in early March 2019 (and not assessed as part of this research), with general availability in 2Q19. Buyers looking for a service provider to also provide major incident response services via an optional retainer will need to leverage a third party via Alert Logic’s partner network.
- Executives looking for a real-time view of the service can leverage the risk-oriented executive dashboard and reports available via the portal. However, buyers who require heavier service management, such as access to real-time SLAs or monthly reports, will need to plan for more involvement with Alert Logic as many of these deliverables are not self-service and are only produced on demand when requested.
- Security monitoring for SaaS is currently limited to Microsoft Office 365 and Salesforce.
- Out-of-the-box compliance reporting options are currently limited to Payment Card Industry Data Security Standard (PCI DSS) and Center for Internet Security (CIS) config benchmarks. Reporting against specific compliance regimes is available by using its log search function along with guided support documents provided by Alert Logic. Additional out-of-the-box compliance reports are on the roadmap to be added.
AT&T
AT&T
is a global telecommunications and IT services provider that offers a
range of security device management, and security monitoring and
response services for large enterprises, midsize businesses and
governments. AT&T is headquartered in the U.S. (Dallas), with
regional offices in the U.K. (London) and Hong Kong. It delivers managed
security services from three 24/7 SOCs (one Europe-based, one
Asia/Pacific-based and one U.S.-based), and four SOCs operating in a
“follow the sun” model to provide 24/7 support during local business
hours (two in the Asia/Pacific region, two in North America). SOCs are
English-speaking, and there is a translation service available for other
languages.
On 22 August 2018,
AT&T completed the acquisition of AlienVault, a vendor with security
information and event management (SIEM), threat intelligence,
vulnerability assessment, EDR and network intrusion prevention system
(IPS) capabilities. On 26 February 2019, a business unit called AT&T
Cybersecurity was created that merges AlienVault’s technology and
services, AT&T Cybersecurity Consulting and AT&T Managed
Security Services. At the time of Gartner’s research for this Magic
Quadrant, AT&T has been actively integrating the AlienVault
acquisition into its MSS business and moving customers from the legacy
AT&T Threat Manager platform to AlienVault Unified Security
Management (USM) Anywhere. Threat Manager customers are now provided a
managed threat detection service via the AlienVault USM web interface
supported by AT&T security experts in its SOCs.
AT&T’s
Threat Manager service is priced by events per day (EPD), with other
network-based services priced based on bandwidth. AT&T offers device
management through discrete managed security offerings for network
security, data and application security, and mobile and endpoint
security. Device management and workflow are handled through the
AT&T Business Center portal. Threat intelligence is now offered
through AT&T Alien Labs, an in-house threat intelligence center than
combines AlienVault’s Open Threat Exchange (OTX) and AT&T’s
visibility into its network. Threat Manager provides data retention for
nine locations around the world to meet data localization requirements
(in the U.S., Ireland, Germany, Japan, Australia, the U.K., Canada,
India and Brazil). Other AT&T MSS offerings provide additional
flexibility including on-premises storage. In 2018, in addition to the
acquisition of AlienVault, AT&T introduced monitoring for AWS and
Azure environments, self-service capabilities for customers of firewall
management, and faster deployment of sensors for MSS delivery.
AT&T
should be considered by organizations with a preference for
telecommunications and security services sourced from a single provider,
and those that require extensive correlation rule and customization
that can be supported by the AlienVault USM platform.
Strengths
- AT&T, in addition to the assets and capabilities acquired with AlienVault, also has a sizable portfolio of managed security services organized according to buyer need — assessing and planning, detection and protection, and response and recover.
- AT&T has expanded its threat intelligence beyond the insight captured via its visibility from its IP connections with the addition of AlienVault (now AT&T Alien Labs OTX) and the large threat-intelligence-sharing community around OTX.
- As might be expected from a SIEM console experience, the reporting and event handling are strong elements of the Threat Manager portal if customers have the resources and skills to take advantage of them.
- AT&T has good visibility with Gartner clients considering discrete MSSs. AlienVault has good visibility as a SIEM product with midsize and smaller enterprises.
Cautions
- At the time of this research, there is a lack of clarity around aspects of the AlienVault acquisition. AT&T has moved rapidly to create a unified business unit and migrate customers to AlienVault USM, but it is too early to tell how customers will react to the new platform (based on a SIEM solution interface). Additionally, AlienVault USM features a large ecosystem of MSSPs leveraging USM Anywhere and USM Appliance. It is not clear how AT&T will rationalize its own Threat Manager business alongside this existing ecosystem of now potentially competitive MSSPs.
- AlienVault is a full-featured SIEM that requires a level of training and expertise to navigate and use, and may not appeal to MSS customers that are looking for a less complicated portal experience. Additionally, customers who have been transitioned to the AlienVault USM Anywhere portal must use a separate portal to address device management functions. AT&T has indicated unifying the portals is on its roadmap.
- AT&T’s MSS business is heavily skewed to the North American market, with far fewer customers in the Europe and the Asia/Pacific markets. Buyers requiring a strong presence in these regions should closely evaluate AT&T’s coverage.
- Customers offered mixed marks for satisfaction with AT&T MSSs, with many below the average compared to its competition. Overall experience and integration marks were lower than the competition, while evaluation and contracting, and service and support were above average.
Atos
Atos
is an IT services-focused organization delivering digital services
globally with 14 24/7 SOCs across Asia/Pacific, Europe and North
America. Atos is headquartered near Paris, with regional offices in the
U.S. (Purchase, New York) and Singapore. Atos provides a wide range of
consulting, system integration, managed services and other offerings
alongside its managed security service portfolio.
In
addition to security event monitoring and response services, Atos also
offers incident response (both remote, leveraging CrowdStrike among
other EDR vendors, and on-premises, as required), and vulnerability
assessment and vulnerability management services. An internal function
provides threat intelligence capabilities for use across its services.
Advanced threat detection is available as part of Atos’ Prescriptive
Security SOC offering using Atos’ proprietary Codex solution as well as
Interset user and entity behavioral analytics (UEBA). In addition,
IT/OT/IoT SOC services are also available. Atos has a strong sales and
implementation function, deployed globally and without the use of
channel partners. Customized requirements from customers drive
implementation time scales of up to six months, which is a process that
involves chargeable consultancy and a specialized team. Atos offers SLAs
that are in line with market norms. The tiered service model, which is
incremental, offers a low-cost Basic tier, as well as the Standard and
Premium service tiers with service options and “bolt on” advanced
packages to suit specific customer requirements.
Atos
is a good shortlist candidate for large European and U.S.-based
multinational corporations that have complex or custom requirements
across a wide sphere of security technology where threat detection and
response, and vulnerability management services are key.
Strengths
- Atos has a range of experience in transformational digital business projects within large enterprises, driven by its wider range of IT services engagements.
- Atos has a well-established model for managing security in IoT-/OT-based environments with existing partnerships with large manufacturers in the space.
- Atos’ security analysts maintain a wide range of operations-focused security qualifications.
- Atos supports a wide range of commercial security technologies with complementary services to manage its outputs and configuration and to promote prevention of threats.
- Atos has introduced a degree of flexibility in its pricing structures enabling the delivery of SaaS-aligned pay-per-use operational models.
Cautions
- Atos focuses on large multinational organizations and does not target its services to midsize enterprises; service pricing caters best for the higher levels of consumption associated with larger organizations.
- Atos’ MSS portal is focused on audit and service management functions, with customer-facing operational requirements directly met by the commercial SIEM product’s own interface.
- Atos has limited support for SaaS applications, developing and supporting functions for widely used applications on a case-by-case basis. Buyers that plan to migrate services to the cloud should consult with Atos to ensure their security monitoring requirements can be met.
- Atos customers report satisfaction with implementation stages, but a lack of ongoing maintenance of functions, through-life evolution and innovation in service delivery.
- Atos is rarely mentioned by Gartner clients interested in MSSs.
BAE Systems
BAE
Systems offers a range of managed security services and cybersecurity
services, including security event monitoring, managed detection and
response, threat intelligence, incident response and vulnerability
management, in addition to advisory and other security solutions. BAE
Systems’ headquarters are located in Farnborough, U.K., with regional
offices in Guilford, U.K., Boston, Massachusetts and Singapore, as well
as Sydney and Dubai. Services are delivered via four 24/7 SOCs located
in the U.S., U.K. and Philippines.
The
BAE Systems offerings focused on security event monitoring and response
are Complete Security Monitoring (CSM) and Managed Detection and
Response (MDR). Additional services include Vulnerability Management
(positioned for enterprise customers) and Vulnerability Scanning Service
(positioned to small and midsize business [SMB] customers), Incident
Response, and Threat Intelligence. BAE Systems Security Management
Console is its portal that provides customers with a single location for
visibility and interaction to BAE Systems’ various services.
In
the past 12 months, the portal has seen improvements focused on
role-based access control (RBAC) and self-service features, log search,
device health and management, and firewall policy management (for
managed UTM customers). Data residency is addressed through a
combination of in-country data centers and Azure regions depending on
where the customer’s data needs to be stored.
MSS
buyers that are looking for a single provider that can offer MSS
combined with MDR should consider BAE Systems, particularly less mature
buyers that also require services for other core security operations
capabilities. More mature buyers, especially those in the banking,
financial and insurance sectors, as well as the government sector, who
are looking to augment their internal capabilities with advanced threat
detection and response should also consider BAE Systems.
Strengths
- BAE Systems’ investments in its platform for advanced analytics, its threat intelligence capabilities and its use of orchestration and automation technologies will appeal to buyers looking for a provider that can address advanced threat detection use cases tailored to their requirements and processes.
- BAE Systems’ can support a range of response activities, particularly when the MDR service is combined with its incident response retainer.
- Threat hunting is now embedded as part of BAE Systems’ CSM and MDR service offerings.
- Customers generally give BAE Systems slightly higher-than-average marks across general satisfaction, product satisfaction, and value for services; however, marks for evaluation and contracting were more mixed.
Cautions
- Vulnerability assessment and management services are not yet standardized. Vulnerability management services are offered through Outpost24, whereas vulnerability scanning is offered through Rapid7.
- Most BAE Systems customers are in North America and Europe. BAE Systems has little footprint in other markets except where its incident response and threat intelligence services are consumed.
- BAE Systems struggles to market itself effectively considering the investment it has made in its MSS infrastructure (e.g., delivery platform and proprietary threat detection technologies).
- The Security Management Console offers more-limited capabilities for investigating and responding to incidents and for compliance reporting than leading competitor portals.
Capgemini
Capgemini
is headquartered in Paris and has large regional offices in Mumbai,
London and New York, as well as locations in 40 other countries.
Capgemini provides a range of managed security services as part of its
Cybersecurity Services business operating under the Capgemini and Sogeti
brands. It has 10 SOCs internationally across Asia, North America and
Europe that are leveraged to deliver services, with an eleventh due to
open this year in Melbourne, Australia.
Capgemini
offers a range of MSSs with security event monitoring and response
powered by IBM QRadar and IBM Resilient, and vulnerability management
that ranges from assessment only through to remediation for IT
outsourcing (ITO) customers. Incident response is available via remote
or dedicated, on-site resources. Threat intelligence is provided via an
internal team that mines customer data for threats, which is
supplemented with third-party threat intelligence. Capgemini has a
global sales force with smaller teams of dedicated security sales
professionals in all major regions providing support to the security-led
areas of wider contracts. The onboarding process can be augmented with
consulting services depending on service and technology requirements.
Capgemini offer basic SLAs and operates service tiers of Bronze, Silver
and Gold, which provide incremental levels of threat detection
capabilities with an option to define tailored requirements outside of
those tiers.
In the past 12 months,
Capgemini has evolved its MSS business, coordinating the Capgemini and
Sogeti businesses and creating a more unified go-to-market approach. On
21 February 2019, Capgemini announced the closing of the acquisition of
Leidos Cyber, which extended its global footprint and services (e.g., OT
and IoT security).
Capgemini is a
good shortlist candidate for large global organizations that require
flexibility and customization at scale in the deployment, integration
and management of security technologies. Those that have localized and
complex security requirements with driving factors such as data
residency should also consider Capgemini.
Strengths
- Capgemini’s portal has been improved to offer a better user experience with a specific focus on customer interaction, reporting and SLA-aligned metrics.
- Capgemini introduced the concept of the “golden hour” as a framework for providing MDR-like capabilities previously agreed with the customer. This construct allows SOC analysts to take predefined actions to contain or disrupt a threat — such as blocking threats on firewalls, SWG, SEG and user account suspension — within an hour of the threat being detected.
- Capgemini offers an established set of IoT/OT offerings predominantly in the manufacturing, automotive and energy sectors.
- Capgemini is able to support a wide range of commercial security solutions.
Cautions
- The roadmap for Capgemini lags many competitors, but it is evolving as Capgemini works to add offerings and capabilities in line with the market. This includes expanding capabilities to cover cloud services (IaaS, SaaS and PaaS), as well as deploying security orchestration, analytics and reporting (SOAR) technologies in its SOCs. The integration of Leidos and how it fits into the roadmap is unclear at this time.
- Capgemini has a standard, but basic, set of SLAs for response and remediation in comparison with the market. These are considered a starting point for negotiating custom SLAs tailored to individual customers and their environments. Buyers will need to determine whether they need custom SLAs, and that these are aligned against their requirements and budgets.
- Capgemini has limited visibility with Gartner clients for MSS-specific deals. Capgemini’s MSS deals are often included as part of end-to-end cybersecurity outsourcing or digital transformation initiatives.
- Capgemini customers are generally satisfied with the service, delivery and product, but its overall ratings were below average compared to the competition.
CenturyLink
CenturyLink
is a telecommunications and public and private cloud service provider
based in Monroe, Louisiana. It has regional offices in Singapore, London
and Buenos Aires, Argentina. CenturyLink has eight SOCs including four
in the U.S., and one each in London, Singapore, Buenos Aires, and India
(Bangalore). The SOCs operate in a blended 24/7 and follow-the-sun
model. There are dedicated North American and U.K. SOCs to support
national government contracts. CenturyLink provides a range of services,
with security event monitoring and response, as well as technology
management services across a broad range of network and host-based
security solutions. Additional services include Vulnerability & Risk
Monitoring that leverages RiskSense and Qualys to provide vulnerability
assessment and management, and threat intelligence services supported
by the recently branded Black Lotus Labs team. Incident response
services, including on-premises support, are available via a retainer.
CenturyLink
uses a combination of proprietary implementations of big data
platforms, commercial products and other tools. Several service tiers
are available, from basic endpoint security management to advanced
threat-oriented capabilities. Some data residency and staff citizenship
requirements can be met with in-region SOCs and data storage. The
pricing model for MSSs depends on the services contracted and includes
set monthly recurring or usage-based fees; for example, threat
monitoring is based on GB-per-day data.
In
2018, CenturyLink completed the integration with Level 3, including the
MSS business. In January 2019, CenturyLink’s expansion into Singapore
was completed with the opening of its eighth SOC. Additionally, the
vendor introduced a mobile app to supplement its MSS portal, added
coverage for public cloud monitoring, and improved its log monitoring
services, which allowed it to deliver cost reductions to customers. It
also introduced several service and pricing options for small and
midsize customers.
Existing
CenturyLink network services customers, from midsize to very large
enterprises, IaaS and cloud service customers, as well as organizations
with global service requirements, should consider CenturyLink for MSSs.
Strengths
- CenturyLink has introduced several options that should appeal to smaller organizations, with service tiers that include basic monitoring for small organizations and no-retainer-needed incident response services to managed firewall customers.
- CenturyLink now also offers free log ingestion of 10 Gb per day and has reduced the price of log ingestion across all levels.
- The MSS portal provides strong role-based controls, including fine-grained role mapping and access for users. Customization of dashboards is also better than typically available from other vendors.
- CenturyLink provides extensive monitoring coverage for SaaS applications with the Cloud Security Monitoring service.
- Reference customers give CenturyLink generally positive marks.
Cautions
- Support for advanced threat detection technologies is not uniform across network, sandbox and endpoint. Network traffic analytics via the CenturyLink network backbone is available globally, but payload analysis is not. Forensics on endpoint is available in the U.S.; packet data forensics is still in the planning stage.
- MDR-style services are not as mature as those available from competitors. For example, managed EDR services are available only in the U.S. Other services are available as customer-specific engagements.
- Potential customers who require access to raw log data via the MSS portal should validate that the very basic capabilities of the CenturyLink portal will meet their needs. The portal still has limited features for capturing and using assets and their business value, and does not support integrations to enable managing vulnerability scans or viewing scan results.
- CenturyLink has low visibility with Gartner clients for stand-alone MSS deals.
Fujitsu
Fujitsu,
headquartered in Japan, has 24/7 SOCs in Japan, the U.S., Singapore and
the U.K., in addition to a few non-24/7 SOCs in other countries
(Finland, Germany and the U.S.). Fujitsu’s marketing and footprint for
MSSs are primarily in Japan and Europe, with some focus on the North
American and Australian markets.
Fujitsu’s
services are focused on a standard set of managed security services,
with security event monitoring and response services available either
through its multitenant LogRhythm platform or deployed on customer
premises as required. Fujitsu offers a number of discrete MSS offerings
centered on management of various security technologies, like network
and web application firewall, intrusion detection system (IDS), cloud
access security broker (CASB), EDR, data loss prevention (DLP), and
identity and access management (IAM). Vulnerability assessment and
management services are available using a variety of popular
vulnerability assessment solutions. Fujitsu’s in-house Cyber Threat
Intelligence (CTI) service leverages a range of feeds — open source,
commercial and third party — that are used as part of its security event
monitoring service. It is available as a stand-alone offering. Incident
response services are offered to complement the MSS offering, and are
offered in blocks of 10 days or via a daily rate.
Fujitsu’s
delivery platform is hosted in Fujitsu data centers. Fujitsu has
introduced a new portal that provides a more traditional MSS experience
compared to the previous portal that was a direct interface into the
LogRhythm management console for security event monitoring services.
Fujitsu offers 365-day raw log and event retention. Raw logs are
archived after 10 days, but retrievable via request to Fujitsu’s SOC.
Buyers
that are looking for flexible service delivery and high-touch
technology management services should consider Fujitsu. Organizations
purchasing other IT or security services from Fujitsu should consider
including it in their MSS procurement shortlists.
Strengths
- Fujitsu has strong partnerships with security technology vendors that allow it to wrap a number of additional services around its security event monitoring and response service.
- The vendor has a strong market presence and reputation in Japan, with good traction among large enterprises. Its presence in Europe is also strong.
- Fujitsu’s flexible service delivery options appeal to large organizations that are heavy on outsourcing most of their security capabilities.
- Fujitsu’s customers give average marks for value and above average for sales professionalism, contract negotiations, and integration and deployment.
Cautions
- Fujitsu’s offerings in emerging areas such as managed detection and response, and security monitoring of public cloud environments are weaker than most competition. For example, Fujitsu collects telemetry from AWS and Azure through log collectors that leverage native APIs, rather than direct API integration from Fujitsu’s platform and the cloud service providers.
- The Fujitsu MSS portal, while improved over the past 12 months, is basic and offers capabilities for creating and responding to service requests and viewing incidents. Key capabilities such as scheduling of vulnerability scans, allowing users to customize reporting and dashboards, and viewing of threat intelligence feeds are not available though.
- Real-time access to raw logs for 10 days is standard, but custom requirements for longer periods can be agreed on a per-customer basis. Fujitsu indicates access to retained logs older than 10 days may take up to five days to complete depending on the size and complexity of the retrieval request.
- Fujitsu is rarely seen in Gartner client inquiries for discrete MSS procurement due to its low brand recognition as an MSSP.
IBM
IBM,
headquartered in Armonk, New York, is both a security technology and
service provider with a range of managed security and other
complementary services via a global network of 24/7 SOCs. IBM has
regional MSS offices in the U.S. (Cambridge, Massachusetts and Atlanta,
Georgia), and in every major region around the world. IBM has five
global, 24/7 SOCs, branded as X-Force Command Centers, and four non-24/7
SOCs.
IBM’s MSS offerings are
focused on security event monitoring leveraging its QRadar SIEM
platform, which provides unified monitoring across the customer base.
QRadar form factors available to customers include shared multitenant
(the default), on-premises, SaaS SIEM, or a hybrid. Other SIEM platforms
(e.g., Splunk or ArcSight) can also be supported as required.
Complementary MSSs from IBM include vulnerability assessment and
vulnerability management through the IBM X-Force Red team, and incident
response retainers, incident preparation, and threat intelligence
services provided as part of the unified IBM X-Force Incident Response
and Intelligence Services (IRIS). A range of advisory and professional
services are also available. IBM recently introduced its X-Force Threat
Management (XFTM) service that provides an integrated threat monitoring,
detection and response service that leverages SIEM (primarily QRadar,
but others are supported as needed), SOAR (via IBM Resilient) and
third-party EDR tools. Support for data residency requirements can be
addressed using the form factors described previously.
In
the past 12 months, IBM introduced a mobile app to complement its
web-based portal. It also improved the analytic and operational
capabilities in its delivery platform and operations through the use of
proprietary analytics, QRadar User Behavior Analytics (UBA) and QRadar
Advisor with Watson (formerly Watson for Cyber Security), and IBM
Resilient.
IBM should be a
shortlist candidate for larger enterprises that are looking for a
full-featured MSS with a global footprint of SOCs that can support a
variety of local languages as required. Existing IBM service customers
should also consider IBM MSS for any shortlists.
Strengths
- IBM offers a strong set of security event monitoring services and related offerings underpinned by the IBM Security technology portfolio. The flexibility afforded by IBM QRadar will appeal to enterprise buyers who are adopting or moving to the cloud.
- IBM has better aligned its complementary services for threat intelligence, incident response and threat hunting among other services by combining them into the IRIS team.
- The introduction of SOAR and advanced features within the QRadar platform for use by the IBM X-Force Security Centers should yield improved threat detection, as well as faster detection and response times.
- IBM’s visibility with Gartner customers and MSSP buyers is oriented toward large enterprises. IBM has good visibility in the MSS market.
Cautions
- IBM’s introduction of a packaged MDR-like service in X-Force Threat Management is a good first step toward creating bundled offerings, but visibility in the marketplace and with Gartner clients has been minimal. Some partnerships, such as integration with Fortinet and Carbon Black have been announced, but additional partnerships have been limited.
- IBM’s Virtual Security Operations Center Portal, while full featured, is starting to lag the competition from a user experience perspective. Customer feedback about the portal is mixed. IBM is promoting use of its mobile app as an alternative means of using the portal.
- Buyers should carefully analyze the technology approach recommended to deliver MSSs (e.g., shared or dedicated QRadar, whether on-premises or hosted) to ensure that the approach is compatible with their IT environments, architectures and requirements.
- IBM’s customer feedback across the board was below average compared to the competition.
NTT
NTT
Security is the specialized managed security service company of the NTT
Group. NTT is headquartered in Tokyo, with regional headquarters for
North America, Europe and the Asia/Pacific regions. NTT operates 10 SOCs
globally across the Asia/Pacific, European and North American regions.
In August 2018, NTT Corporation announced a new holding company
structure that will integrate NTT Communications, Dimension Data, and
NTT Security into a new global business later in 2019. NTT DATA will
continue as a stand-alone, listed company that collaborates with NTT.
NTT’s
operating model utilizes the group companies to sell and manage
relationships for clients who are delivered managed security services
centrally via NTT Security. NTT MSSs provide delivery of all threat
detection services (Threat Detection Enhanced and Enterprise Security
Monitoring), as well as services for technology management and
vulnerability assessment in all major regions. NTT offers a single
service management interface to customers that provides security
incident communications and case management. NTT offers incident
response services that include enhanced response to threats where
firewall management is performed by NTT Security and/or managed EDR is
consumed by the customer. An incident response retainer, along with
incident response planning and forensic services, is also available. NTT
has an in-house Global Threat Intelligence Center providing internally
consumed threat intelligence for MSSs, as well as stand-alone offerings
like its Reputational Threat Services.
NTT’s
security offerings focus on different levels of service interaction
defined by the criticality of incidents as opposed to providing defined
service tiers. Customers will receive high levels of analyst interaction
on critical events and electronic notification for all others.
In
the past 12 months, NTT has implemented its unified portal leveraging
ServiceNow, integrated with the main service desk functions across NTT,
and announced strategic partnerships with Symantec to provide new
services like Web Security as a Service (WSaaS).
NTT
appeals to larger enterprises who have purchased separate IT and
networking services from other NTT group companies and those who are
completing wider digital transformation projects or have specific,
complex requirements that will be served across the portfolio of NTT
Group companies.
Strengths
- NTT can serve a wide range of industries/verticals across geographies due to the global presence of NTT Group companies.
- NTT’s strategy involves investing in security technology, as evidenced by its acquisition of WhiteHat Security, as well as an industry-aligned commitment to continue research and development of its services portfolio and capabilities, like advanced analytics.
- NTT has moderate visibility with Gartner clients looking for discrete MSSs.
- NTT’s customers provide above-average marks for several ratings like overall experience, evaluation and contract negotiations, integration and deployment, and overall service and product capabilities.
Cautions
- NTT Security is an operational unit that utilizes the NTT Group companies to sell and market its delivered services. This approach has created confusion for some Gartner clients when renewing existing MSS agreements that were originally purchased from entities prior to the formation of NTT Security (e.g., Solutionary or NTT Com Security). Postrestructuring, this concern may abate as NTT becomes more unified without individual operating companies. Clients should monitor the situation as it progresses.
- The NTT portal is now primarily powered by ServiceNow, which provides a basic ServiceNow-style experience for many functions, like case management and ticketing; however, other legacy portals are used to provide an interface into features like log management and portal user management. APIs are available to integrate into customer environments, like case management solutions, as required.
- NTT Security’s managed EDR offering is a work in progress. NTT Security currently supports FireEye, which will expand to include Carbon Black and CounterTack, which was previously announced as a partnership in November 2017.
Secureworks
Secureworks,
is headquartered in Atlanta, Georgia, with offices in London, Sydney,
Tokyo and Edinburgh, Scotland. It provides a range of security event
monitoring and response services, in addition to technology management,
vulnerability assessment and management, threat intelligence, managed
detection and response, incident response (via retainer), and consulting
services. MSSs are delivered from three 24/7 SOCs in the U.S. (Atlanta;
Chicago; and Providence, Rhode Island); one 24/7 SOC in Kawasaki,
Japan, one SOC in Edinburgh, Scotland and one in Hyderabad, India. The
SOCs are supported by a center of excellence in Romania.
MSS
delivery is through Secureworks’ proprietary Counter Threat Platform
(CTP) that provides data collection and management, analysis, and the
portal. Secureworks also has premises-based physical and virtual
appliances to support log aggregation/transmission and network security
monitoring. The Secureworks Client Portal provides access to services
for customers. Secureworks offers customers seeking EDR services the
option of fully managed services using the Red Cloak agent, or monitored
EDR for Carbon Black and CrowdStrike. An additional service for
proactive threat hunting is available at an hourly rate or for customers
using the Red Cloak agent via Advanced Endpoint Threat Detection Elite
with Active Threat Hunting. There is an add-on service for malware
detection delivered in partnership with Lastline. The Secureworks
Counter Threat Unit (CTU) threat research and development team provides
threat intelligence to support a variety of MSS offerings, as well as
stand-alone threat intelligence services. MSS pricing is based on the
number and type of event sources in scope for monitoring or management.
Secureworks recently introduced additional pricing models for service
bundles, such as its MDR service bundle that is priced by number of
employees in the buyer’s organization.
In
2018, Secureworks introduced the ability for customers to easily link
their ServiceNow with the Secureworks portal, and additional APIs enable
customers to integrate MSSs with the customers’ security operations
infrastructure. Self-service provisioning gives customers control over
which devices to bring into the scope of MSS monitoring. Secureworks
also introduced its Security Maturity Model to help customers by
measuring and monitoring improvements in customers’ security operations
capabilities.
Secureworks should be
considered by midsize through to global enterprise organizations
seeking an established MSS with a consistent, shared delivery approach
that offers additional complementary security operations capabilities
delivered as a service.
Strengths
- Secureworks offers an incident response retainer that is popular with buyers, which provides proactive as well as remote and on-site reactive response services.
- Secureworks’ bundling of existing services to form its MDR offering, with a simpler pricing structure based on employees and assets, has gained initial traction with Gartner clients.
- Security orchestration and automation has been integrated into the Counter Threat Platform for SOC analysts and operations, with continued expansion of capabilities, both internal and customer facing planned over the next year.
- Secureworks has very high visibility with Gartner clients, and is frequently included in competitive MSS deals by North America-based midsize and enterprise buyers. It also has good visibility with U.K. buyers.
- Gartner customers largely give strong positive feedback for Secureworks’ MSS offerings across service and product quality, sales, implementation and support compared to the competition.
Cautions
- Secureworks has lower visibility compared with competitors for buyers in continental Europe and the Asia/Pacific region for MSSs.
- Support for customer access to raw logs via the Secureworks portal for investigation and reporting is limited. Customer that require great access to logs, and long-term retention for compliance requirements must store those on-premises or in their cloud in third-party log management appliances supported by Secureworks.
- Monitoring of SaaS solutions is still limited and support for CASB solutions is not available. Office 365 and Salesforce are supported. SaaS solutions such as Box, Dropbox, Workday and G Suite are not supported, although support for identity solutions like Okta and OneLogin are available.
- Some Gartner small and midsize customers report frustration with Secureworks’ service delivery and account management, which they sometimes characterize as “we are too small to get attention.” Midsize and smaller enterprises should confirm how the service relationship and management process will operate and support their requirements.
Symantec
Symantec,
headquartered in Mountain View, California, is a security technology
company that also offers a variety of security event monitoring services
and complementary services as part of its Cyber Security Services
business. Symantec has regional and country-level offices across the
globe. It operates a global network of SOCs to provide 24/7 global
coverage. Symantec offers a globally standardized approach to how its
SOCs are operated, including their processes and procedures. Symantec’s
Cyber Security Services core offerings address security event monitoring
and response services. They also provide threat intelligence, and
incident response and retainer services. All MSS agreements since July
2017 include the base terms and conditions providing MSS customers
access to Symantec’s incident response retainer with zero upfront cost.
Customers pay for use of the retainer on an as-needed basis. Symantec
also offers Managed EDR, Managed Network Forensics, and Managed Cloud
Defense using Symantec’s own technologies. A managed intrusion detection
and prevention (IDP) service and a service providing security
monitoring for OT and IoT devices are also available via technology
partnerships and Symantec’s own technologies. Symantec’s delivery
platform has been migrated from an on-premises data center to AWS, and
includes its log collection and management, analytics, and customer
portal.
Over the past 12 months, in
addition to the delivery platform move to AWS, Symantec introduced
several services that take advantage of the Symantec technology
portfolio; for example, its Managed EDR service. It also implemented
internal operational improvements to enhance the context around detected
threats; for example, better mapping IP to host and speeding malware
analysis and investigation.
Symantec
MSSs should be on the shortlist for enterprise-size buyers who require
regional support in North America, EMEA and Asia/Pacific, as well as
existing Symantec technology customers who want managed security
services for their existing technology investments.
Strengths
- Symantec has recently migrated its delivery platform to AWS. Beyond allowing it to take advantage of the benefits of using IaaS and AWS services, it will also enable Symantec to use AWS Regions to address data residency requirements, which was previously handled through contractual agreements.
- Symantec’s technology portfolio for endpoint, network and cloud security are now being leveraged through standardized offerings in the MSS catalog. Existing Symantec customers using these technologies and looking for a service option will be well-supported, as will MSS buyers looking for a single provider for solutions and 24/7 monitoring and response.
- Symantec is a visible competitor for MSS buyers in North America, EMEA and Asia/Pacific, and has good visibility as a shortlist candidate with Gartner clients.
- Customers rate Symantec above average compared to competition for overall experience, evaluation and negotiations, integration and deployment, and service and support.
Cautions
- Buyers looking for a vulnerability management service to complement monitoring and response services will need to leverage a third-party service. Support for providing vulnerability assessment data for use in the security monitoring and response services is mixed. Qualys is presently supported through direct API integration; however, other vulnerability assessment vendors require manual upload of data.
- Buyers that require their MSS hold an SOC certification should confirm the status. Symantec’s certifications are a work in progress as they transition from SOC 1 Type II to SOC 2. Certifications like ISO 27001 and PCI service provider are current as of the data of this research.
- Symantec’s marketing of its Cyber Security Services is lagging competitors. Symantec is primarily known as a technology company and marketing of its MSS offering is not visible when compared to the software side of the business, e.g., there is visibility of technology partnerships with competing MSS firms, but no visibility of the same services being offered by Symantec MSS.
Trustwave
Trustwave,
headquartered in Chicago, also has key offices in London, Singapore,
Sydney and Tokyo among others. It delivers MSSs from 24/7 SOCs in
Singapore; Manila, Philippines; Warsaw, Poland; Chicago; and Denver,
Colorado; with a few other non-24/7 SOCs across the world. As part of
the Singtel Group, Trustwave has a strong reach across EMEA and
Asia/Pacific in addition to North America.
Trustwave
offers conventional managed security services such as 24/7 security
event monitoring and vulnerability management. In addition, Trustwave
Managed Detection and Response (MDR) for Endpoints service offers
managed Carbon Black and Cybereason EDR, as well as Darktrace for
network detection and response. Managed threat hunting is also an option
under the MDR set of services. Trustwave has made efforts to integrate
the MDR service with its more established service areas both in terms of
workflow and in offering pricing benefits to customers that choose
both. The MDR service can address response actions via EDR that can be
handled remotely in less than four hours with a certified digital
forensics and incident response handler. For on-site incident response
services via retainer, Trustwave offers consulting services through its
SpiderLabs Digital Forensics and Incident Response Team. The SpiderLabs
team within Trustwave also has an in-house threat intelligence
capability that the company leverages for threat detection; but it does
not sell this as a stand-alone feed to customers. Trustwave has several
proprietary products that it can manage for customers (such as WAF, UTM,
IDS), and it also supports several third-party technologies for
monitoring and management.
Over the
past 12 months, Trustwave has been integrating the stand-alone Singtel
and other MSS businesses under the Trustwave brand, including a
rebranding launch in December 2018. Trustwave introduced updates to its
TrustKeeper portal in 2018, which is the primary delivery platform for
the MSS. The logs and events from monitored/managed infrastructure
elements are forwarded on to Trustwave’s multitenant platform that
stores data in a number of its global SOC locations. Trustwave can
enable local data residency by maintaining local instances of its portal
within AWS Regions.
Trustwave is a
good shortlist candidate for buyers, ranging from midsize enterprises
to large, global enterprises, who are looking for standard managed
security services with some additional advanced capabilities like threat
hunting and MDR, and other complementary services.
Strengths
- The updated TrustKeeper portal offers good role-based access, language localization, custom report/dashboard creation capabilities and visibility into ticket workflow. Integration of the service workflow with customers’ Slack and ServiceNow environments is a positive feature, particularly for large organizations with dispersed teams.
- Trustwave has a strong threat intelligence capability through its SpiderLabs team, and good professional services offerings that complement its MSS and MDR offerings.
- The vendor’s threat detection capability is focused on analytics that delivers use cases based on a combination of Trustwave proprietary technology and TensorFlow libraries.
- Trustwave places an emphasis on global consistency in service delivery and leveraging a point of delivery (POD) concept to provide more customer-specific attention and a vertical focus.
Cautions
- Though Trustwave supports CASBs and collects data through native APIs in Microsoft Azure and AWS, it still lags some competitors in offering cloud-specific MSSs like vulnerability and asset management, container security and cloud security posture management.
- Though Trustwave has a global presence, its go-to-market approach in Singapore and Australia still needs better alignment with the global Trustwave platform strategy. The organizational realignment that happened in 2018 is yet to be fully realized in the field.
- Trustwave’s MDR service is most visible via its managed EDR offering. The managed network detection and response with Darktrace and other vendors is not as visible in the market. Customers desiring a full MDR service that spans endpoints and network security need to confirm with Trustwave how it can support that requirement from both a supported vendor and integration-of-service perspective.
- Trustwave customers reported general satisfaction, but below-average marks compared to the competition across overall experience, evaluation and contracting, integration and deployment, and service support and product capabilities.
Verizon
Verizon
is a telecommunications company headquartered in Basking Ridge, New
Jersey, with regional offices in Reading, U.K., and Sydney. Verizon
offers a range of MSSs and security consulting services using a global
network of SOCs. Local business hours (i.e., “follow the sun”) SOCs are
located in Ashburn, Virginia; Dortmund, Germany; and Canberra,
Australia. It also has an SOC in Luxembourg that is dedicated to
customers with specific data sovereignty requirements. The vendor’s 24/7
MSS SOCs are located in Chennai and Hyderabad, India. Customer data is
stored in operations centers located in the U.S., Europe and Australia.
Verizon’s
Unified Security Portal (USP) provides single-portal access across all
services and capabilities for customers. Verizon’s MSS platform includes
log management capabilities allowing clients to search 90 days of
stored logs. Verizon’s MSS delivery platform includes open-source,
proprietary, and commercial technologies including Splunk security data
analytics, Elasticsearch for log search, and Verizon’s proprietary
correlation engine and Local Event Collector (LEC). MSS pricing is based
on the volume of log data ingested per day, with distinct pricing for
advanced detection services. For services based on endpoint detection
and response products, the pricing is per endpoint; and for network
analytics, it’s per the number of flows ingested. Verizon also offers
additional services like an incident response retainer, Autonomous
Threat Hunting (via the Niddel acquisition), and the Verizon Risk Report
(VRR).
In 2018, Verizon introduced
the Verizon Risk Report, a new service to augment its MSS offerings.
VRR provides daily quantitative assessments of a customer’s security
posture based on Verizon threat intelligence, and oriented toward
security portfolio decision makers. Verizon also acquired ProtectWise in
March 2019, which provides network traffic analytics and forensics
capabilities.
Enterprises and
public-sector organizations, including existing Verizon network
customers, should consider Verizon if they require well-established
global or region-specific MSSs.
Strengths
- Verizon offers a broad range of additional security services including VRR, distributed denial of service (DDoS) protection and incident response services, among others like the Autonomous Threat Hunting service.
- The portal offers excellent capabilities for searching incidents and logs to support investigations, extensive roles and access controls for portal users, as well as strong visualization and dashboard customization. The portal provides flexible and comprehensive log searching capabilities to end users, and there is extensive and granular support for defining and managing portal roles.
- Verizon offers several services that support advanced threat detection and response, with an emphasis on network-based capabilities.
- Verizon has good visibility with Gartner clients for MSSs.
Cautions
- Some MSS portal functions lag those of competitors or require additional service levels to access. Users must request reports for predefined compliance schemes from the Verizon SOC, and the portal offers MSS customers limited threat intelligence. Greater access to these capabilities requires the Verizon Risk Report services.
- Verizon supports data residency requirements with its own resources in Asia/Pacific, Europe and North America. Customers with these requirements in Africa and the Middle East and in Latin America and South America must engage with Verizon partners in the region to support them, or leverage Verizon’s Managed SIEM offering.
- Verizon relies primarily on Netskope CASB to monitor SaaS environments, although Cisco Cloudlock CASB is also supported. Only Office 365 is supported natively (via APIs). If other SaaS applications are able to generate and forward their own logs and events, they can be monitored.
- Customer feedback for Verizon is satisfactory, but below average compared to its competition in areas at the beginning of the buying and onboarding stages, such as preselection activities, negotiations, and integration and deployment.
Wipro
Wipro
is headquartered in Bangalore, India and has 24/7 SOCs in India (8),
Europe (2), North America (4) and the Middle East (1). As a global IT
services provider, Wipro has a significant incumbent customer base to
which it can position its MSS offering.
Wipro’s
standardized security monitoring service is based on IBM QRadar
(delivered in a federated, on-premises model) and Demisto SOAR (powering
automation in its SOCs). In addition, Wipro offers vulnerability
assessment management services through a partnership with Qualys. Data
from vulnerability assessment scans is made available to customers
through Wipro’s MSS portal. Wipro also offers advanced MSS offerings for
IDS/IPS, network traffic analytics, network forensics, EDR, deception,
breach and attack simulation, and SaaS monitoring via a robust set of
technology partnerships. The company also offers several types of
professional services to complement its MSS offering, such as incident
response, threat hunting, forensics and malware analysis.
Over the past 12 months, Wipro has focused on internal operational improvements, and service measurement and reporting.
Wipro
is a good fit for customers that are looking to consume a range of
services (spanning consulting, implementation and outsourcing) from the
same provider. Incumbent Wipro customers and organizations looking for
more flexibility in their service approaches should consider Wipro as a
shortlist candidate.
Strengths
- Wipro offers a good combination of standard and advanced managed security service offerings, leveraging its strong partnerships with established and emerging security technology vendors.
- Wipro can cater to regional data residency requirements due to its focus on local log collection and analytics, as well as a strong global network of SOCs.
- Wipro has strong incident detection and response SLAs that are above average in the industry.
Cautions
- Wipro’s MSS portal is still not as user-friendly as the competition — customer self-service options to manage the state and status of an event are limited.
- Despite the use of on-premises QRadar to store customer logs and perform detections, the Wipro portal offers limited access to logs by customers. There is a limited search capability, or users can request log reports from the SOC. Users with sufficient expertise can be given access to the QRadar console for direct searching.
- Wipro has low visibility with Gartner clients and MSS buyers.
Vendors Added and Dropped
We
review and adjust our inclusion criteria for Magic Quadrants as markets
change. As a result of these adjustments, the mix of vendors in any
Magic Quadrant may change over time. A vendor’s appearance in a Magic
Quadrant one year and not the next does not necessarily indicate that we
have changed our opinion of that vendor. It may be a reflection of a
change in the market and, therefore, changed evaluation criteria, or of a
change of focus by that vendor.
Added
Alert Logic
Dropped
BT, DXC Technology, HCL Technology and Orange Business Services.
Inclusion and Exclusion Criteria
To qualify for inclusion in this Magic Quadrant, managed security services providers must:
- Offer remotely delivered 24/7 security event monitoring and response services, delivered via a common, shared delivery platform that is owned, hosted and maintained by the provider, which is consumed by at least 70% of their customers; however:
- Customers that consume services that are not delivered remotely, e.g., on the customer premises, or that are delivered remotely on a one-to-one basis per customer, are not applicable.
- Customers that do not consume security event monitoring services, e.g., technology-only and device-management-only customers, are not applicable.
- The delivery platform must include the following capabilities at a minimum: log/data collection and management; analytics for threat detection use cases; reporting for compliance use cases and service management; case management and ticketing; and a web-based portal to consume and interface with services. However:
- Providers’ platforms that lack multitenancy characteristics (e.g., leverage common compute, storage, software and management) will not be included.
- Providers that deliver their services in a one-to-one model (e.g., leveraging a customer’s own SIEM solution), on a per-customer basis, even if the technology to deliver the service is hosted for the customer by the provider, e.g., managed and hosted SIEM solution, will not be included.
- Delivery platforms can be proprietary, leverage third-party technology (e.g., commercial off-the-shelf [COTS]), or a combination of the two. Providers that leverage a delivery platform that is owned, hosted, operated and maintained by a third party to deliver MSSs will not be included.
- Customer interface options beyond a web-based portal, such as real-time chat, war rooms and mobile applications are not required, but may be considered if they enhance the value proposition.
- Offer at least two of the following services that highly complement security event monitoring and response offerings:
- Incident response services (e.g., via a retainer with the buyer)
- Threat intelligence services (not just machine-readable threat intelligence [MRTI] or reselling third-party MRTI)
- Vulnerability assessment and management services
- Managed detection and response (e.g., managed endpoint detection and response)
- Have an SOC in two or more regions where security event monitoring and response services are fully supported and delivered. However:
- SOCs specifically designated for delivering services other than security event monitoring and response, such as providing only technology administration and management, will not be included.
- SOCs that deliver security event monitoring but are dedicated to a specific customer base (e.g., government-only customers), while not specifically included for regional scope requirements, may be considered if they enhance the value proposition.
- Provide evidence via region-specific marketing materials of sales, either directly or via a channel, being performed in three or more regions (North America, Latin and South America, Europe, Middle East and Africa, and Asia/Pacific).
- Have at least 500 customers globally consuming remotely delivered security event monitoring and response services as defined previously, with a minimum of 100 customers in each of two or more regions (North America, Europe, Asia/Pacific, Middle East and Africa, and Latin and South America).
- Have minimum annual revenue of $50 million that is generated from shared, remote security event monitoring and response services. Revenue generated by services such as technology administration and management, consulting, professional services, and technology reselling are not to be included in the above threshold.
- In-scope service offerings and technology (e.g., a delivery platform) features and functionality must be generally available (and being sold, if a service) to MSS buyers as of 1 November 2018.
- Be service providers that Gartner determines to be significant vendors in the market because of their market presence or service innovation.
Evaluation Criteria
Ability to Execute
Product/Service
refers to the services offered, and their capabilities, for security
event monitoring and response, such as the delivery platform that
includes log collection and management, analysis, and customer interface
methods. It also includes highly complementary services, such as
vulnerability management, threat intelligence, incident response, and
managed detection and response services.
Overall Viability (Business Unit, Financial, Strategy, Organization)
includes an assessment of the organization’s overall financial health,
as well as the financial and practical success of the business unit. It
views the likelihood of the organization to continue to offer and invest
in the product as well as the product position in the current
portfolio.
Sales Execution/Pricing
addresses the service provider’s success in the market and its
capabilities in presales activities. This also includes MSS revenue,
pricing and the overall effectiveness of the sales channel. The level of
interest from Gartner clients is also considered.
Market Responsiveness and Track Record
evaluates the match of the MSS offerings to the functional requirements
stated by buyers at the time of acquisition. It also evaluates the
MSSP’s track record in delivering new functions when the market needs
them.
Marketing Execution
evaluates the service provider’s ability to effectively communicate the
value and competitive differentiation of its MSS offering to its target
buyer.
Customer Experience
evaluates the service delivery to customers. The evaluation includes
ease of onboarding, the quality and effectiveness of monitoring and
response activities, and reporting and problem resolution. This
criterion is assessed by surveys of vendor-provided reference customers,
Gartner’s Peer Insights, as well as by feedback from Gartner clients
that are using the MSSP’s services, or that have completed competitive
evaluations of the MSSP’s offerings.
Operations
addresses the MSSP’s service delivery resources, such as
infrastructure, staffing and SOC operations. It also includes evaluation
of external operations reviews, and relevant certifications and
attestations.
Completeness of Vision
Market Understanding
involves the MSSP’s ability to understand buyers’ needs and to
translate them into services and capabilities. MSSPs that show the
highest degree of market understanding are adapting to customer
requirements. MSSPs with market-leading vision are investing in
expertise and technology to monitor and analyze a customer’s diverse
range of environments (i.e., on-premises, IaaS and SaaS), as well as the
external threat environment to better understand the sources, motives,
targets and methods of attackers. They are also developing and
introducing services that support large-scale data collection; advanced
analytics, including statistical and behavioral functions; and
monitoring of new data sources. The goal of these capabilities is to
more effectively reduce the mean time to detect a threat, and also to
drive the mean time to respond to a threat for customers. MSSPs are also
keeping pace with regulatory requirements customers may face across
different geographies.
Marketing Strategy
evaluates the clear, differentiated messaging consistently communicated
internally and externalized through social media, advertising, customer
programs, and positioning statements; and is tailored to the specific
client drivers and market conditions in the MSS market.
Sales Strategy
addresses selling that uses the appropriate networks including: direct
and indirect sales, marketing, service, and communication. It includes
partners that extend the scope and depth of market reach, expertise,
technologies, services and their customer base.
Offering (Product) Strategy
evaluates the vendor’s approach to product development and delivery
that emphasizes functionality and delivery options as they map to
current and emerging requirements for MSSs. Development plans are also
evaluated.
Business Model covers the design, logic and execution of the organization’s business proposition to achieve continued success.
Vertical/Industry Strategy
evaluates the strategy to direct resources (sales, product and
development), skills, and products to meet the specific needs of
individual market segments, including verticals.
Innovation
refers to the service provider’s strategy and ability to develop new
MSS capabilities and delivery models to uniquely meet critical customer
requirements.
Geographic Strategy
evaluates the vendor’s strategy to direct resources, skills and
offerings to meet the specific needs of geographies outside the “home”
or native geography, either directly or through partners, channels and
subsidiaries, as appropriate for that geography and market.
Table 2: Completeness of Vision Evaluation Criteria
Evaluation Criteria | Weighting |
|---|---|
Market Understanding | High |
Marketing Strategy | Medium |
Sales Strategy | Medium |
Offering (Product) Strategy | High |
Business Model | Not Rated |
Vertical/Industry Strategy | Medium |
Innovation | High |
Geographic Strategy | Medium |
Source: Gartner (May 2019)
Quadrant Descriptions
Leaders
Each
of the service providers in the Leaders quadrant has significant mind
share among organizations looking to buy MSSs as a discrete offering.
These providers typically receive positive reports on service and
performance from Gartner clients. MSSPs in the Leaders quadrant are
typically appropriate options for enterprises requiring comprehensive
portal-based access for interfacing with the service (e.g., responding
to alerts, incident management, workflow, reporting, asset and access
management, and managing other procured services, like incident response
and vulnerability management) along with interaction with the MSSP for
analyst expertise and advice.
Challengers
In
the Challengers quadrant, Gartner customers are more likely to
encounter MSSs that are offered as components of an IT or network
service provider’s (NSP’s) other telecommunications, outsourcing or
consulting services. Although an MSS is not a leading service offering
for this type of vendor, MSSs in these markets have a stronger Ability
to Execute.
Visionaries
Companies
in the Visionaries quadrant have demonstrated the ability to turn a
strong focus on managed security into high-quality service offerings for
the MSS market. These service providers are often strong contenders for
enterprises that require access to and support for “cutting edge”
technology, flexible service delivery options and strong customer
service. MSSPs in the Visionaries quadrant have less market coverage
compared with vendors in the Leaders quadrant.
Niche Players
Niche
Players are characterized by service offerings that are available
primarily in specific market segments, or primarily as part of other
service offerings. These service providers often tailor MSS offerings to
specific requirements of the markets they serve. This quadrant is also
characterized by providers that are newer, or that have expanded beyond
local and regional markets to the global MSS market, and are maturing
their delivery capabilities and offerings.
Context
Organizations
should not use this Magic Quadrant in isolation as a tool for selecting
providers. Gartner provides a range of toolkits and geographically
contextual research to assist buyers in correctly scoping and
administering an MSS selection process. MSS buyers are increasingly
challenged to identify and select the best provider for their needs.
Prior to starting the process to outsource security operations to a
service provider, it is critical buyers understand their desired
outcomes, use cases and requirements. (See “Foundational Elements to Get Right When Selecting a Managed Security Service Provider” and “How to Work With an MSSP to Improve Security.”)
When
goals, use cases and requirements are not focused on prior to engaging
with an MSS, an all too common result is dissatisfaction with the
provider and MSS experience. Based on feedback from Gartner clients and
MSS buyers over the past 12 months, the most common elements of
dissatisfaction often stem from misaligned expectations and the scope of
the services provided.
It is
important that prospective MSS buyers focus on the outcomes they require
to ensure they purchase the right services offered by the right type of
providers. Buyers that require 24/7 threat detection and response use
cases should highly weight an MSSP’s capabilities in those areas, in
addition to its in-house threat research and intelligence capabilities.
Complementary services like incident response retainers may be of
importance too. MSS buyers who have requirements related to specific
technologies and capabilities should focus on providers who are better
at providing customization, where appropriate, in addition to
standardized services.
As a result
of the requirements of Gartner clients and the direction of the MSS
market, Gartner has made changes to the inclusion criteria in this
year’s Magic Quadrant. Comparisons to previous years is not advised (nor
is a year-over-year comparison of vendor position in the Magic Quadrant
generally advised). Additionally, vendors that no longer meet the
inclusion criteria should still be considered when there is a need for a
partner in specific regions, as well as for highly customized and
specific offerings focusing on technology deployment and integration.
Market Overview
The
MSS market is mature, with an estimated market size of $10.7 billion in
2018. The market continues to adapt to the challenges facing
organizations around:
- An increasingly complex IT environment that includes SaaS and IaaS, and the expansion into nontraditional IT domains
- The growing hostile external landscape
- The ongoing issues of a lack of talent and expertise in security
- The needs of less mature organizations that are likely to have only ever implemented preventative security controls
These
challenges are driving organization’s to focus on and improve their
threat detection and response capabilities. For many organizations, the
use of an MSSP enables achieving that goal.
The
MSS market has a set of providers whose core business is often not
security-focused, such as IT outsourcers, system integrators and
telecommunications providers. For such providers, there is an increasing
focus on maturing and expanding their offerings to meet changing market
demands. Alongside the pure-play security service providers, there are
now hundreds of smaller, geographically focused MSSPs and MDR service
providers around the world offering detection-led and highly competitive
services. Every week a new provider is visible in the market; either a
net new provider or a provider in an adjacent market that has added
managed security services. These services vary according to:
- The core business they operate under (e.g., managed IT services or IT outsourcing, system integration, telecommunications, security technology or pure-play security services)
- Geographic and vertical markets being targeted
- The targeted buyer by size and maturity
This
Magic Quadrant reflects the requirements of Gartner clients as well as
the evolution of the global MSS market. Market trends, which are
discussed in more detail below, include:
- The adoption of core security capabilities where historic investment has been weak, for example vulnerability management, threat intelligence and incident response.
- Moving beyond monitoring of only on-premises technologies as more organization adopt SaaS and IaaS, as well as the move by many organization to include security event monitoring and response services for OT and IoT under the remit of security operations.
- Increasing segmentation of MSSPs focused on delivering a broad portfolio of managed security services to address the wide range of needs by larger enterprises versus those who are focused on core security operations activities.
- Portals as the primary interface with MSSPs, but delivery models being expanded to include other channels, like mobile devices.
- The inclusion of direct response to security events and issues and MSS provider’s adoption of emerging technologies, like SOAR, which have the potential to transform how MSSPs deliver services in the future.
There
are other adjacent markets providing security services to address the
core use case for 24/7 threat detection and response. Increasingly MSSPs
are pivoting to compete with these markets to address buyer demands by
offering the following services:
- Managed detection and response services: Organizations are looking to address a lack of 24/7 threat detection and response — especially where there is lower maturity, and little to no investment in detection technologies and the experts needed to use those tools and perform incident response activities. Thus, MDR services are filling the demand (see “Market Guide for Managed Detection and Response Services”). Midsize enterprises are gravitating to MDR when looking for a turnkey service that fits their needs. More mature organizations with defined security operations teams look to MDR to fill gaps in their coverage, e.g., through services like managed EDR or threat hunting. MSSPs have reacted to these needs by offering services primarily focused on managed EDR and threat hunting, as well as expanded incident response services. Many of these services are customized; few are standard offerings integrated into the core MSS business.
- Remote SIEM solution management and co-management: Larger enterprises that have invested in a SIEM solution with plans to build their own 24/7 operations, or organizations that are concerned about data residency requirements, are increasingly turning to MSSPs to take over management, operation and use of their SIEM solution. For some MSSPs, this is becoming their preferred approach as they may also be a technology reseller and integrator. Thus, they end up selling the SIEM solution to the customer, and then provide managed security services using the customer’s newly deployed SIEM solution. However, many organizations will look to an MSSP to help them when there are failed SIEM deployments, change in business direction, changing plans about building out their own SOC, and so on. Rather than lose a large deal, some MSSPs are increasingly accommodating these buyers even though it does not align with their preferred delivery model (i.e., use the MSSPs standard delivery platform).
- Customer-owned SOC: In some geographies like the Middle East and India, regulatory requirements drive buyers toward an on-premises SOC. In other geographies, on-premises SOCs are driven less by regulations and are more about the risk tolerance of the organization, its scale and nuances of its business that makes it avoid outsourcing services to an MSSP. However, building an SOC is not a small endeavor and requires expertise to build, then operate and run an SOC. Many MSSPs are also offering a service where the SOC may be fully managed on-premises by the MSSP, or a hybrid model where some remote services are provided from a shared customer SOC alongside some on-premises staff.
Core Services for Detection and Response, Against a Broadening MSS Market
A
MSS looks significantly different now compared to what it was just five
years ago. At the core of most MSSP services portfolios is 24/7
security event monitoring and response, of varying degrees of maturity
and sophistication. This will not change. Organizations have awoken to
the need for detection and response capabilities, underpinned by
continuous monitoring and visibility, to complement their investment in
prevention and blocking technologies. (See Figure 2. Adaptive Attack
Protection in “Seven Imperatives to Adopt a CARTA Strategic Approach”).
In
addition to security event monitoring and response capabilities, the
need for good security hygiene or “the security basics” is also being
recognized by many organizations. Capabilities like vulnerability
management and the use of threat intelligence are still challenging for
many organizations. Vulnerability management is evolving toward a
risk-based approach, but few MSSPs are adapting to this shift. Most
still support basic vulnerability scanning. (See “Implement a Risk-Based Approach to Vulnerability Management.”)
Once,
the focus of a security monitoring service was to ensure a threat was
simply detected and alerted to. Now, being alerted to a threat is no
longer sufficient for many organizations. Once a threat is identified,
organizations are looking to service providers to take on a more active
role. For some organizations that have an existing security team and
internal incident response and handling expertise, only an alert may
still be acceptable. Even so, the expectation now is that the alert will
be context-rich relative to both the threat (e.g., broad-based malware
or targeted attack, or part of a known malware campaign or threat actor)
and the customer’s vertical and organization. (For example, was the
targeted asset critical to the buyer? Were there unpatched
vulnerabilities on the targeted asset? What’s the “blast radius” of the
attack inside the organization?)
For
other organization that have little to no security team and a lower
security operations maturity, the expectations are that the MSSP will do
more than just issue an alert and let the customer fend for itself.
They need the MSSP to take an active role in analyzing, triaging, and
then disrupting or containing the threat, i.e., they need the MSS to act
as a first-level incident responder for them. The feedback from
customers surveyed as part of this Magic Quadrant indicates that 49% of
them still only get alerts as the primary form of response from their
MSSP. However, 43% indicated the MSSP is taking a more active role in
the response to a detected threat, either helping with containment
(e.g., a more MDR-style service) or getting involved in the end-to-end
detection through to containment and remediation (usually when the buyer
has a broader ITO agreement with the MSSP).
If
an attack was not detected and contained quickly enough, then it is
important to have an incident response retainer that can provide
targeted incident response services as well as support in the event of a
potentially large incident. (See “Market Guide for Digital Forensics and Incident Response Services.”) Buyers are increasingly looking to their MSS to offer these capabilities as part of a more end-to-end service delivery model.
Response
services beyond those described previously are being adopted by
organizations on an as-needed basis to address gaps in their
capabilities or to align to organizational strategy to leverage
outsourcing providers where feasible. For some buyers, technology
management is still an important element of managed security services.
But that need is being filled by a wider variety of services providers
depending on the type of technology and the delivery of the technology.
We see the commoditization of technology management reaching its peak.
Firewalls are increasingly being managed by telecommunications service
providers as a network device. Endpoint protection is being managed by
managed services providers (MSPs). And, the adoption of cloud-delivered
security solutions (aka security as a service), like SWGs and SEGs,
firewalls and DNS security, further erodes the value of managed
technology services for buyers. (For example, when using security as a
service from the cloud, the need for a provider to perform health,
performance and availability monitoring, as well as software upgrades
goes away as it’s now the technology provider’s responsibility.)
Depending on their core verticals, MSSPs are being left to perform
policy management or to expand into technology management for
technologies that are not commonly delivered “as a service.” Gartner
clients indicate it is challenging to find, afford and retain the
expertise to operate and use technologies like SIEM, EDR and network
traffic analytics [NTA] solutions.
Increasingly,
the portfolios of many MSSPs are quite extensive as they look for
opportunities to expand and stay “sticky” with buyers. This has both
positive and negative implications for MSS buyers. For those
organizations looking to outsource a wide variety of security
operations, extensive MSSP portfolios are beneficial. However, this
choice also must be tempered by concerns about whether an MSSP will
become more of a generalist considering the broad range of technologies
that it may need to manage and monitor. (It is estimated that an MSSP
has to potentially support hundreds of different vendors and solutions.)
Threats No Longer Target Only On-Premises IT
As
organizations move to the cloud, IT environments become more complex
because of SaaS and IaaS. These cloud environments also increase the
attack surface for organizations due to their complexity. Even
capabilities like vulnerability management and log management in these
environments require new skills and expertise that are not readily
available in the market. MSSPs are being pushed to address the threats
against these environments, but the variability across providers is
still quite large. The monitoring of public cloud services —
specifically AWS and Azure — is maturing, with basic security event
monitoring available from many MSSPs. But monitoring other cloud
providers, as well as offering services oriented specifically at other
aspects of cloud environments (like monitoring for threats against
containerization and microservices) are in their infancy.
Over
the last couple of years, many MSSPs have improved their capabilities
around integrating with, and consuming log and data outputs from, SaaS
vendors, especially the common solutions like Office 365, Salesforce and
Workday. However, many MSSPs are just applying basic use cases to SaaS
(for example, looking for brute force attacks on accounts). Some MSSPs
are addressing specific risks, like business email compromise (BEC), and
looking for anomalous administrative activities; but this is not yet
consistent. Outside of these SaaS applications, MSS buyers will be
forced to leverage solutions like CASB and an MSS that can support the
preferred CASB vendor. This will be needed at least until more API
access from the SaaS vendors is available and MSSPs are able to support
those vendors. (See “Market Guide for Cloud Access Security Brokers.”)
Operational
technologies, like industrial control systems (ICSs) and supervisory
control and data acquisition (SCADA), are increasingly being targeted.1
This is driving organizations to apply more scrutiny to their OT
environments, and security operations teams are being pressed to expand
their coverage into the OT environments, including asset and
vulnerability visibility, and threat detection and response. (See “2018 Strategic Roadmap for Integrated IT and OT Security.”)
IT is very different from OT, and the skills available in the market
are nascent. Additional risks like safety, privacy and resiliency are
also concerns (see “OT Security Best Practices”).
MSSPs, similar to cloud service providers, are being pushed by buyers
and existing customers to help address these risks. However, it is still
very early days. There are a number of OT- and IoT-specific security
technologies available on the market (see “Market Guide for Operational Technology Security”),
and some MSSPs have established partnerships. Yet many of the services
being introduced are highly customized and have not hit peak demand to
warrant transferring them into formally established service offerings in
MSS portfolios. Buyer due diligence is warranted to validate the claims
being made by MSSPs about their available OT and IoT security services.
The Segmentation of the MSS Market Is Increasing
The
MSS market is increasingly segmenting between those MSSPs that are
primarily interested in buyers that need customization around technology
and services, and those that just want a traditional shared delivery
approach. Many MSSPs are aligning to one of these types of buyers, and
less commonly are targeting both.
MSS buyers can generally be grouped as:
- First timers and low-security operations maturity organizations — These are organizations that have never leveraged MSSs, or may be lower on the maturity curve. They tend to focus on 24/7 threat detection and response, and complementary services only, leaving the provider to use their preferred delivery approach (i.e., a delivery model and platform shared across the customer-base). This is where much of the MSS buyer market currently exists.
- Digital transformers — These are organizations, usually large or very large global organizations, with varying degrees of security operations maturity, who need to improve their current security operations capabilities as part of larger, IT digital transformation projects, e.g., moving IT toward the use of cloud services. (See “Driving Digital Business Transformation for Industry Leadership: An Executive Perspective”).
- SOC builders — These are organizations that want their own SOC, but lack the skills, expertise and time to build it themselves. These buyers may already own a SIEM solution. They want a provider that can build and support the SOC, either in a short-term model until the buyer can run it themselves (usually up to 12 months) or continually in an ongoing support capacity (fully outsourced or in a hybrid model).
- High-maturity augmenters — These organizations have made significant investments in people, processes and technology in their security operations, but are looking for opportunities to hybridize the operations by leveraging services providers.
- Compliance-focused buyers — These organizations simply want to meet the requirements of a common compliance standard to satisfy auditors, customers or trading regulations.
System
integrators and IT outsourcers are increasingly targeting the digital
transformers and SOC builders. These target organizations have specific
technology-based approaches in mind and are looking for a partner that
can provide assessments via consulting activities; recommend, architect,
sell, and implement buyer-preferred technologies; and then operate and
run those technologies for the buyers. These projects tend to be
large-scale, cross-IT, multiyear efforts where the scale of activities
(including MSSs) align to the provider. The first timers and
high-maturity augmenters who make up the majority of Gartner clients
want an outcome that provides monitoring, detection and response as a
service. This is usually achieved through the use of shared services
that have been optimized for delivery efficiency and are at lower price
points compared to one-off and customized services.
Mobile Apps Are Emerging, but Portals Are Still Important
The
number of MSSPs also offering a mobile application has increased over
the past twelve months (e.g., Atos, CenturyLink, IBM and Secureworks).
This is expected given the always-connected nature of organizations and
the needs of multiple personas. For example, a CISO or CIO who may
travel frequently and is not tethered to a laptop will benefit from
any-time access to the status of the services from the MSSP. Security
operations analysts who may participate in an on-call rotation as part
of the incident response capability will benefit from the expediency
when something is alerted to afterhours. They can get their phone, open
an app and start to review the incident details, rather than having to
find their laptop, connect and log into the MSSP portal, and locate the
case or ticket. Obviously both use cases allow for more frequent access,
if not interaction, with the MSSP. Mobile apps are not yet ubiquitous
and the experience varies widely, so validating the mobile app
experience of the provider, if important, should factor into the
requirements for selecting an MSSP.
Portals
to interface with an MSSP have not disappeared, nor has their usage.
MSS buyers surveyed for this Magic Quadrant indicated 40% still use the
MSSP portal daily and 26% use it at least weekly. The experience across
MSSPs still varies though in light of this usage by customers. Magic
Quadrant reference buyers in this research were generally neutral or
just satisfied with the capabilities of their MSSP’s portal to support
the day-to-day use of the portal to interface with the MSSP services.
MSSPs who have been in this market for many years still offer the most
mature portal experiences. Providers in markets like IT outsourcing tend
to put less emphasis on the portal, favoring the portal to be used for
service management above offering SIEM-like features that are required
by security teams. (See “Critical Capabilities for Security Information and Event Management.”)
MSS Is Starting to Be SOAR-Powered
It’s
still early days for SOAR, but the promise of improving the
efficiencies and consistencies of SOC activities, as well as being able
to offer more customized processes to MSS customers is compelling. (See “Innovation Insight for Security Orchestration, Automation and Response” and “Preparing Your Security Operations for Orchestration and Automation Tools.”)
Some MSSPs have adopted SOAR technologies in earnest and have embedded
them at the core of their delivery platforms. Based on conversations
with SOAR technology vendors and MSSPs, we expect most MSSPs to adopt
and embed SOAR capabilities over the next three years.
So
what does this mean for MSS buyers? SOAR is not a panacea for MSS
buyers. As this stage, SOAR technologies will be used by MSSPs to make
their analysts more efficient and more productive (and happy) by
removing mundane activities. If properly leveraged, customer experiences
with their MSSs should improve when it comes to consistency and
repeatability of agreed processes. Theoretically, the detection of
threats should improve if MSSP SOC analysts are given more time to
investigate and triage suspect events (e.g., reducing the number of
false positive alerts to customers). In the future, automated response
actions initiated by the MSS to the customer’s own technologies to
reduce the mean time to respond might be a reality (but that’s in the
infancy stage right now).
Evidence
1 “Triton Is the World’s Most Murderous Malware, and It’s Spreading.” MIT Technology Review
Evaluation Criteria Definitions
Ability to Execute
Product/Service: Core
goods and services offered by the vendor for the defined market. This
includes current product/service capabilities, quality, feature sets,
skills and so on, whether offered natively or through OEM
agreements/partnerships as defined in the market definition and detailed
in the subcriteria.
Overall Viability: Viability
includes an assessment of the overall organization's financial health,
the financial and practical success of the business unit, and the
likelihood that the individual business unit will continue investing in
the product, will continue offering the product and will advance the
state of the art within the organization's portfolio of products.
Sales Execution/Pricing: The
vendor's capabilities in all presales activities and the structure that
supports them. This includes deal management, pricing and negotiation,
presales support, and the overall effectiveness of the sales channel.
Market Responsiveness/Record: Ability
to respond, change direction, be flexible and achieve competitive
success as opportunities develop, competitors act, customer needs evolve
and market dynamics change. This criterion also considers the vendor's
history of responsiveness.
Marketing Execution: The
clarity, quality, creativity and efficacy of programs designed to
deliver the organization's message to influence the market, promote the
brand and business, increase awareness of the products, and establish a
positive identification with the product/brand and organization in the
minds of buyers. This "mind share" can be driven by a combination of
publicity, promotional initiatives, thought leadership, word of mouth
and sales activities.
Customer Experience: Relationships,
products and services/programs that enable clients to be successful
with the products evaluated. Specifically, this includes the ways
customers receive technical support or account support. This can also
include ancillary tools, customer support programs (and the quality
thereof), availability of user groups, service-level agreements and so
on.
Operations: The
ability of the organization to meet its goals and commitments. Factors
include the quality of the organizational structure, including skills,
experiences, programs, systems and other vehicles that enable the
organization to operate effectively and efficiently on an ongoing basis.
Completeness of Vision
Market Understanding: Ability
of the vendor to understand buyers' wants and needs and to translate
those into products and services. Vendors that show the highest degree
of vision listen to and understand buyers' wants and needs, and can
shape or enhance those with their added vision.
Marketing Strategy: A
clear, differentiated set of messages consistently communicated
throughout the organization and externalized through the website,
advertising, customer programs and positioning statements.
Sales Strategy: The
strategy for selling products that uses the appropriate network of
direct and indirect sales, marketing, service, and communication
affiliates that extend the scope and depth of market reach, skills,
expertise, technologies, services and the customer base.
Offering (Product) Strategy: The
vendor's approach to product development and delivery that emphasizes
differentiation, functionality, methodology and feature sets as they map
to current and future requirements.
Business Model: The soundness and logic of the vendor's underlying business proposition.
Vertical/Industry Strategy: The
vendor's strategy to direct resources, skills and offerings to meet the
specific needs of individual market segments, including vertical
markets.
Innovation: Direct,
related, complementary and synergistic layouts of resources, expertise
or capital for investment, consolidation, defensive or pre-emptive
purposes.
Geographic Strategy: The
vendor's strategy to direct resources, skills and offerings to meet the
specific needs of geographies outside the "home" or native geography,
either directly or through partners, channels and subsidiaries as
appropriate for that geography and market.
© 2019 Gartner,
Inc. and/or its affiliates. All rights reserved. Gartner is a
registered trademark of Gartner, Inc. and its affiliates. This
publication may not be reproduced or distributed in any form without
Gartner's prior written permission. It consists of the opinions of
Gartner's research organization, which should not be construed as
statements of fact. While the information contained in this publication
has been obtained from sources believed to be reliable, Gartner
disclaims all warranties as to the accuracy, completeness or adequacy of
such information. Although Gartner research may address legal and
financial issues, Gartner does not provide legal or investment advice
and its research should not be construed or used as such. Your access
and use of this publication are governed by Gartner’s Usage Policy.
Gartner prides itself on its reputation for independence and
objectivity. Its research is produced independently by its research
organization without input or influence from any third party. For
further information, see "Guiding Principles on Independence and Objectivity."